A new technique might enable malware to lead to a Fake iPhone Shutdown and discreetly snoop on users
By- Bhavesh Dhake, Security Aficionado
Researchers have revealed a fresh approach for malware on iOS to achieve persistence on an infected device by impersonating its shutdown system, making it impossible to physically determine if an iPhone is off or not.
The NoReboot discovery comes from mobile security firm ZecOps, which discovered that it is possible to stop and then replicate an iOS rebooting procedure, fooling the user into assuming that the phone has been shut off while, in reality, it is still running.
A San Francisco-based corporation known as It's known as the ultimate persistence problem. You can't patch it because you're not exploiting any persistent flaws. "All you have to do is perform a trick on the human mind."
NoReboot works by interfering with the routines used by iOS to shutdown and restart the device, effectively preventing them from ever occurring in the first place and allowing a trojan to gain persistence without really turning off the device. It is a sophisticated strategy since, in most cases, once malware infects iOS devices, it can be eliminated simply by restarting the system. In this manner, the invader is erased from memory. Because the gadget is never truly shut off, the new tactic stops malware from achieving its objectives.
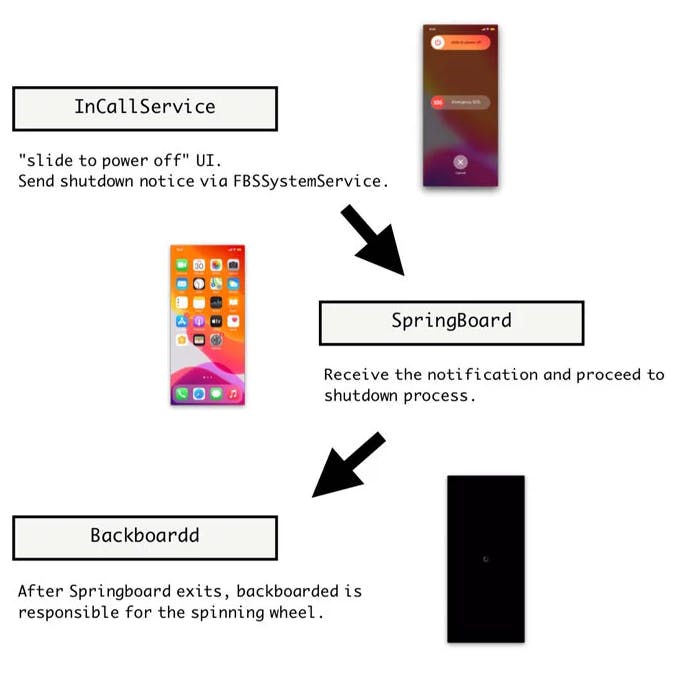
This is accomplished by injecting specially crafted code into three iOS daemons, namely the InCallService, SpringBoard, and Backboardd, in order to feign a shutdown by disabling all audio-visual cues associated with a powered-on device, such as the screen, sounds, vibration, the camera indicator, and touch feedback.
To put it another way, the goal is to give the impression that the device has been turned off without actually turning it off by hijacking the event that occurs when the user simultaneously presses and holds the side button and one of the volume buttons while dragging the "slide to power off" slider.
"Despite the fact that we stopped all physical input," The researchers noted, "the phone remains completely functioning and capable of maintaining an active internet connection." "Because the user is deceived into thinking the phone is off, either by the victim or hostile actors using 'low battery' as an excuse, the malicious actor might remotely influence the phone in an obvious fashion without worrying about being discovered."
The malware strain then forces the SpingBoard, which refers to iOS's graphical user interface, to exit (rather than the entire OS), followed by commanding the BackBoardd, the daemon that handles all touch and physical button click events, to display the Apple logo effect if the user chooses to restart the phone while the malicious code remains active.
Furthermore, this technique could theoretically be extended to manipulate an iPhone force restart by intentionally causing the Apple logo to appear a few seconds earlier when such an event is recorded via the Backboardd, fooling the victim into releasing the side button without genuinely triggering a force restart.
Although no malware has been detected or publicly documented using a method similar to NoReboot, the findings show that once an adversary has gained access to a target device, even the iOS restart process is vulnerable to being hijacked, which is well within the reach of nation-state groups and cyber mercenaries alike.
"Without persistence exploits, non-persistent attacks attained 'persistence,'" the researchers found. A proof-of-concept (POC) attack demonstrating NoReboot is available on GitHub.
